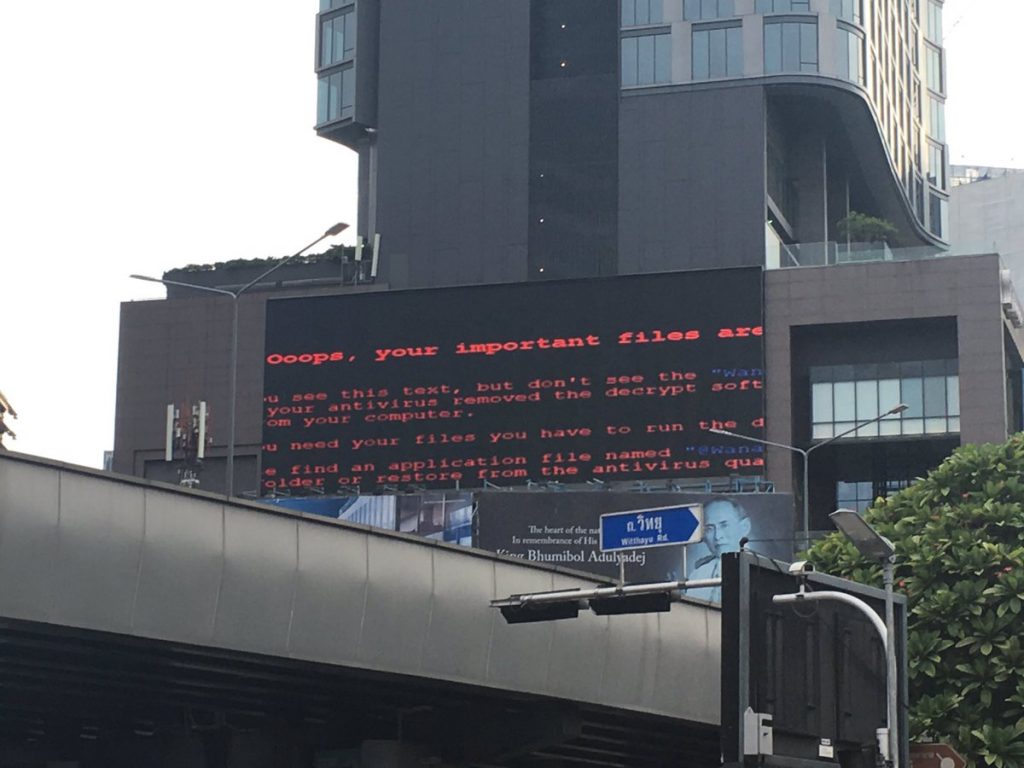
This week’s #AxisOfEasy had a few topics lined up, such as comedian John Oliver’s epic rant about net neutrality crashing the web servers of the U.S FCC (again), but forget all that. Everything has taken a back seat to the WanaCrypt0r (a.k.a “WanaCry”, or “WannaCrypt”) Ransomware Worm. WanaCry broke out overnight May 11th and quickly became the biggest ransomware attack in history. (Ransomware is malicious software which infects your computer or server and encrypts all your files until the victim remits a “ransom”, usually paid via bitcoin, to obtain the decryption key).
What makes WanaCry different from previous ransomware attacks is that it is a worm, where until now ransomware was typically delivered via email phishing and malware delivery.
Let’s get started.
“The future is already here. It’s just unevenly distributed” — William Gibson
In this issue:
- WannaCry Worm leverages previously leaked NSA exploit kit
- Worm stopped when researcher discovered a domain name “killswitch”
- New variants already appearing
- What you can do about it
WannaCry Worm leverages previously leaked NSA exploit kit
The May 1st edition of #AxisOfEasy talked about DoublePulsar the NSA exploit kit leaked by the Shadow Brokers and how it was being used to create new attacks that were infecting unpatched Windows IIS servers.
A part of that leaked framework (called EternalBlue) has now been used to create a ransomware “worm”, the first of it’s kind, to infect those same types of vulnerable Microsoft servers (using a weakness in the Windows SMB service). The worm broke out overnight May 11 and quickly infected upwards of 50,000 to 100,000 hosts going into the weekend, affecting telecoms, hospitals, rail services and numerous other corporate systems.
Microsoft had already released a patch to specifically address the DoublePulsar leak, they have now issued guidance (here, and here), including another emergency patch in the wake of the worm.
Worm stopped when researcher discovered a domain name “killswitch”
While WanaCry infections were concentrated in Europe, over 100 countries reported incidents within the first 24 hours. The worm was on track to spread even more virulently until a security researcher known only by the handle “MalwareTech” discovered a “killswitch” in the code which would stop the worm from spreading. That killswitch was in the form of a non-existent domain name. Instances of the worm would check if it existed, if not they would continue to propagate themselves wherever possible. However if they found that the domain (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[dot]com) did exist, they would stop spreading.
The researcher promptly registered this killswitch domain, thus causing the spread to stop – for the time being.
Events further took on a resemblance to a futuristic cyberpunk novella when parties unknown fired up a Mirai botnet (that’s the IoT device botnet that caused the mother of all DNS outages back in October) and DDoSed the killswitch domain in an effort to kill the killswitch so that the worm could continue its spread.
It is posited that the appearance of new variants without such a killswitch is only a matter of time.
New variants already appearing
At least two variants have already appeared over the weekend:
- one containing another killswitch simply consisting of some other random looking domain, which was duly registered by security researchers again,
- another containing no killswitch, but other faulty coding has prevented it from enacting the encryption component of it’s ransomware payload.
Not to be confused with the “Jaff” ransomware, which is just as bad
As dramatic as this past weekend’s events have been, this type of thing has been going on for years and it’s not limited in scope to Microsoft servers, it frequently comes in via email and targets many and all system types.
For example, over the weekend another ransomware variant, called “Jaff” did spread via email. It uses the same executable name as WanaCry, further confusing security researchers efforts. Any media reports stating that Wanacry was spreading via email spearphishing attacks are almost certainly mistakenly referring to the “Jaff” ransomware.
Jaff” emails have PDF attachments with embedded Microsoft Word docs containing hostile macros which connect to remote URLs that initiate the ransomware download and infection sequence. Subject lines lately are typically about “Invoices”:
Subject: 27_Invoice_9018
What you can do about it
If you’re running a Windows IIS server, make sure you’re up on patches and read the aforementioned Microsoft guidance.
If you aren’t already backing up your systems, you should seriously do that. (At the risk of veering into infomercial territory, we are working on “easyBackup”, should be ready this summer). If you are already running backups, run more backups.
Run antivirus and malware protection, I use Sophos, Bitdefender and ClamAV. If I ever get an unrecognized attachment that gets through our virus filters, blackholes, and my own computer’s antivirus systems that I think I need to open I also run it through Virustotal, a handy online scanning tool that let’s you scan a specific single file.
Previously on #AxisOfEasy
If you missed the previous issues, they can be read online here:


Leave a Reply