 Yesterday, egregious financial truth-tellers (and easyDNS client) ZeroHedge broke the news that parties unknown engineered what looks to be a textbook “pump-and-dump” on Twitter’s stock by putting up a fake “Bloomberg Financial News” site on the domain bloomberg.market and proceeded to run a story on it about Twitter being acquired.
Yesterday, egregious financial truth-tellers (and easyDNS client) ZeroHedge broke the news that parties unknown engineered what looks to be a textbook “pump-and-dump” on Twitter’s stock by putting up a fake “Bloomberg Financial News” site on the domain bloomberg.market and proceeded to run a story on it about Twitter being acquired.
The story spread and shares of Twitter stock promptly spiked on volume, Twitter finishing the day on nearly double the average daily volume.
The reason it can be safely assumed that this was a pretty ingenious pump-and-dump was the purchase, as Zerohedge reveals the day before of quite a few near-the-money call options on Twitter stock with a strike price of $37. Those calls went solidly into the money on the circulation of the fake story. (You know, sort of like all those put options some lucky parties unknown bought on American Airlines just before 9/11)
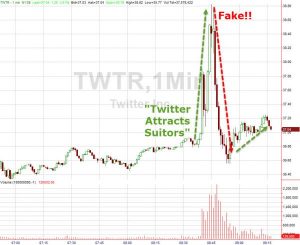 As news of the ruse spread (theDomains reported on it as did many other domaining sites), the price reverted back to it’s pre-pump value and later in the day the .market registry operator Rightside took down the domain and released a statement that the action was in accordance with their standard operating procedures.
As news of the ruse spread (theDomains reported on it as did many other domaining sites), the price reverted back to it’s pre-pump value and later in the day the .market registry operator Rightside took down the domain and released a statement that the action was in accordance with their standard operating procedures.
This case underscores one of the biggest headaches about the new gTLDs is that the sudden, dramatic expansion of the root namespace (now over 1,000 top level domains and counting) make it effectively impossible to “defend one’s marks” in all available TLDs.
TLDs such as .email, .company, .support are attactive phishing targets. Remember that when you get the next “reset your apple ID” email from “apple.support”.
It’s a double edged sword in many respects: even if a company wanted to move some of their functionality out to an aptly matching TLD, say perhaps, http://easydns.support there are more public incidents of this type of thing being a phish or a hoax than there are legitimate rebrands or function shifts to new TLD URLs – companies wanting to do this face an uphill battle.
It makes me realize that I left out a couple important “winners and losers” from my guest editorial on Domain Name News a few years ago “Who Will Be The Winners and Losers of the New TLDS?”
The Losers:
Legitimate Companies: that really do want to rebrand or use new TLDs will have to shout louder and spend more on marketing to out muscle the ever increasing background hum of phishes, scams and frauds passing off on new TLDs.
Target Companies: who will face ever increasing phishing attacks. As Canadian antispam legend (who now works for Apple’s abuse department) Neil Schwartzman told me after I suggested Apple re-register a new TLD phishing domain we had just deleted:
Would that we could re-register all the cousins. We see literally hundreds/day.
It becomes effectively impossible to defend one’s mark’s via defensive registrations (something I said a long time ago which new TLD players are beginning to understand)
So what happens now?
The Winners
Criminals: When you combine all these new perfectly named labels for spearphishing your targets and combine it with ICANN mandated policies that effectively make it mandatory to be vulnerable to them, a new golden age has begun.
DANE: There’s going to have to be a way to authenticate the “reality” of any given website other than looking at the domain name and guessing that it’s legit. This goes beyond DNSSEC signed zones – which basically guarantees that when you ask for a DNS response for “example.com” you really get a response from “example.com”‘s nameservers and that they’re real responses. Somebody could register example.support and email all of example.com‘s customers and simply DNSSEC sign example.support as well.
No, you need something else, something you can hook into the website your customers are used to visiting and somehow asserting that “it’s the real site”. SSL typically fills this role, but SSL costs money, even the cheap certs, which in a 1000+ channel TLD-verse makes it “expensive” by definition.
I think what we’ll see happen is major browser support for DANE (DNS-based Authentication of Named Entities) and a major adaptation of it across the industry.
But we’re not there yet. There’s a big
{{{{ SOMEHOW }}}}
which still needs to be filled in, where example.com will (see above: somehow) “assert” which associated domains in other TLDs are legit and which ones aren’t. Almost like a Sender Policy Framework (SPF) (which specifies what hostnames, domains and IP blocks are permitted to originate email for a given domain) for “related domains” – like:
example.com asserts that:
- example.ca is the Canadian portal for Example Co
- example.support is a real support site for Example Co.
- example.xxx is a blocking website under .xxx
- example.wtf is reserved for Example Co’s April Fool’s japes
- etc.
Either this already exists and I don’t know about it, or it should exist and the absolute clusterfsck of grief these new TLDs are already causing will make it happen.
(P.S On easyDNS you can already setup DANE’s TLSA records under the “Other” records section in your control panel).


Leave a Reply