On Saturday July 13 we became aware that some easyDNS and Zoneedit customers were receiving Paypal phishes via the host iem.easydns.com:
Subject: RE : Supicious Transaction July 14, 2019, 12:07 am test198@m****r.**
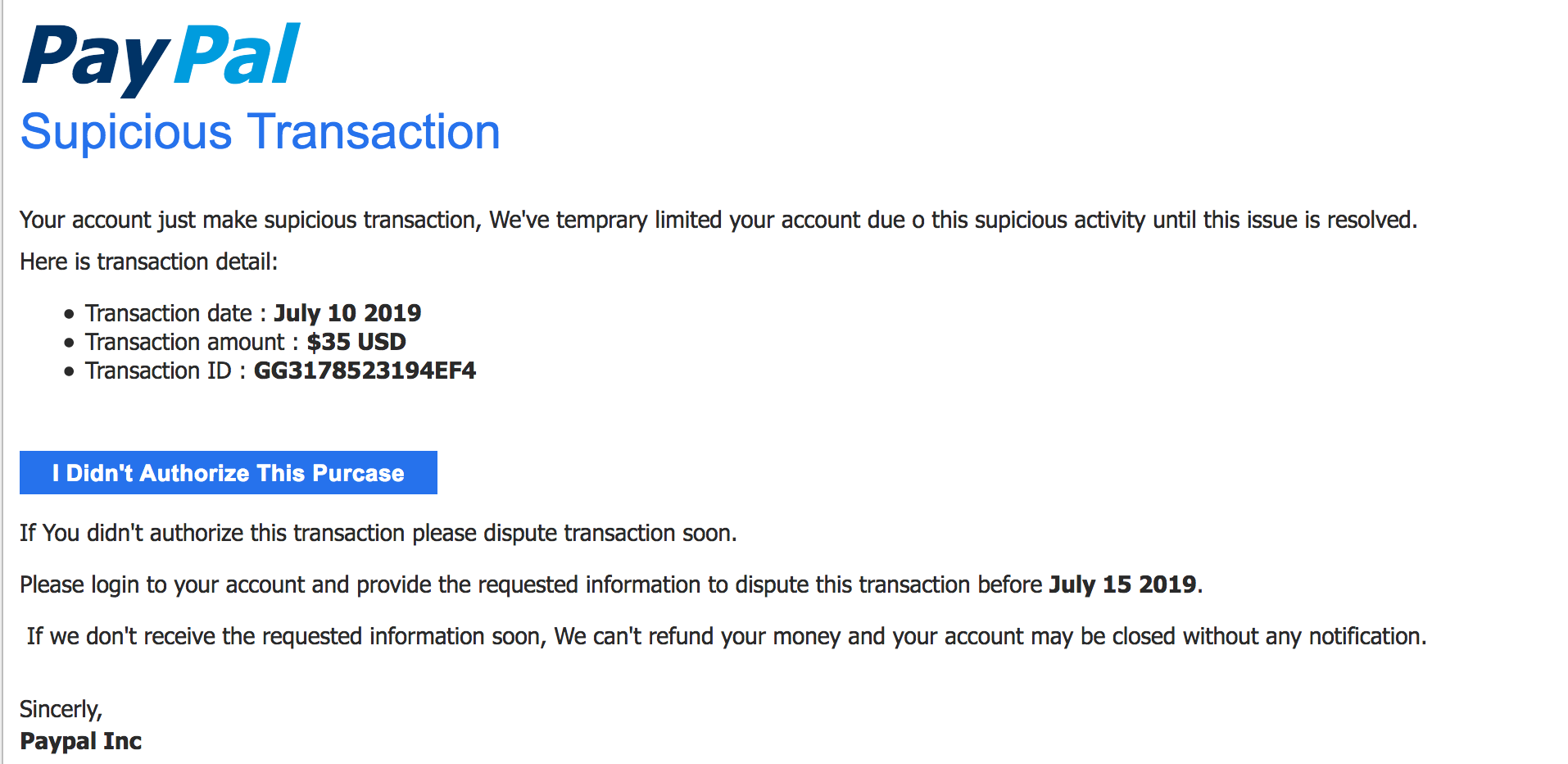
They were certainly phishes and not really from Paypal. Fortunately most people know how to spell the word “suspicious” and would expect any official email from Paypal to get it right (to be clear though, Paypal would never send an email like this, and they would never put a call-to-action button like this within their message to you).
What is embarrassing is that iem.easydns.com is in fact one of our servers that we used to run our self-hosted copy of Interspire Email Marketer, a CRM for broadcast emails. It should have been shut down, it wasn’t, and since Interspire themselves sunset-ed Email Marketer, it’s no longer supported and out of date.
In other words, it was ripe for the taking, which it was, and was used to send these phishes.
What Data Was Affected
The only data stored on IEM were email addresses. We would export segment lists from the within the core DMZ, load them up on IEM, create our messages and let them rip. Further, no other access was gained to any other component of the easyDNS system. Once the problem was discovered the instance was immediately shut down.
A total of 16,879 unique emails were sent this message, 185 to easyDNS users and the remainder to Zoneedit.
What is perhaps even more embarrassing was that this same exact thing already happened once before, in 2015. At the time IEM was still supported by Interspire, so after upgrading and patching it, we changed our procedure so that whenever we created a new email segment, we would delete it after we used it in case something like this happened again.
Somewhere along the line, the procedure broke down, and we failed to delete previously used segments. Then when we stopped using the IEM instance and didn’t shut it down, by the time it was compromised those segments were still there.
We’re sorry and chagrined that this happened again.


I received one of these just minutes after renewing the domain it referenced. Even the amount was very close but… not exact. That was flag #1.
Flag #2 was when I inspected the link. Ya, it was a Russian .RU link. I think I tracked it back to a government domain. Anyway, I knew it wasn’t legit so off to the SPAM bin.
Thanks for the explanation, Mark