
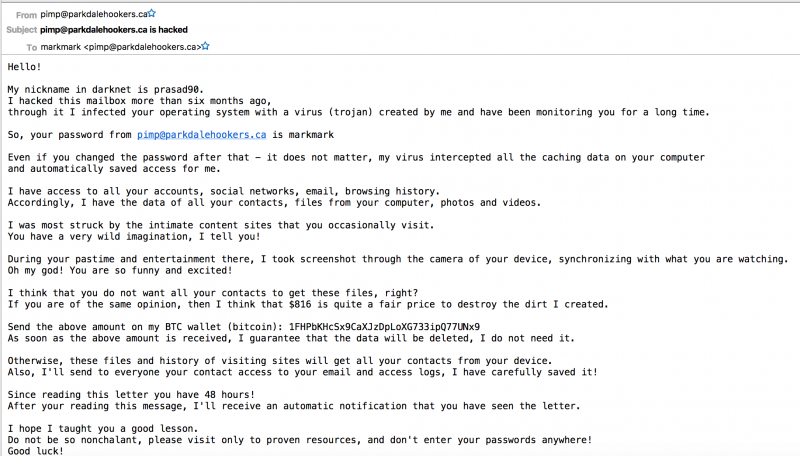
We originally reported on this back in #AxisOfEasy 58, it’s the phenomenon of getting an email spam wherein the mailer claims to have hacked or compromised your computer, and will (pick one).
- encrypt or corrupt your computers, files or data
- spread embarrassing or compromising information about you to your contacts
- release an unflattering video ostensibly taken via your computer camera
Since about a week ago there has been a noticeably large spike in the volume of these spams. I’m personally getting around a half-dozen per day, and clients are getting them and emailing us asking what to do about it.
Most of these emails send you one of your passwords that you may have really used previously (or God forbid, are still using somewhere) as “proof” of their claim to have utterly owned your computer.
How They Do It
So how do these guys know your password, or one of your old passwords, if the claim that they’ve hacked your computer is just a bluff?
Some vendors store passwords in clear text. It’s a major security #fail to do so, but a lot of companies do it anyway. Alternatively, there’s a lot of old, decrepit sites that used to do it, but are still online and vulnerable.
Those vendors and old websites get hacked, and then those login creds get distributed, aggregated and otherwise passed around. There is a thriving market for these on the darkweb. (The chatter within a security list I’m on posits that most of these are being culled from a LinkedIn breach, also noting that many of the recipients are unaware that there even was a LinkedIn breach…although I’m getting lots to addresses that don’t even have LinkedIn accounts.)
easyDNS maintains our own database of around a couple billion credentials as do other security types, and we periodically check our member accounts against it and force password resets on anything that hits. You can also sign up at a place like HaveIBeenPwned and they will email you when your email comes up in a new breach (it’s free).
How To Tell If It’s a Real Ransomware Attack
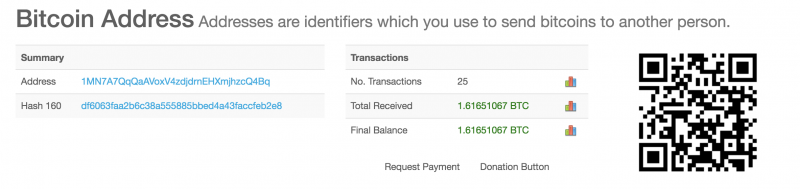
If it’s just an email in your mail and providing an old password, it’s spam and almost certainly a bluff. Don’t fall for it. Some people are. I randomly picked a Bitcoin address from these emails and can see that it’s had 25 transactions totally over 1.6 BTC, currently over $13,000 CAD.
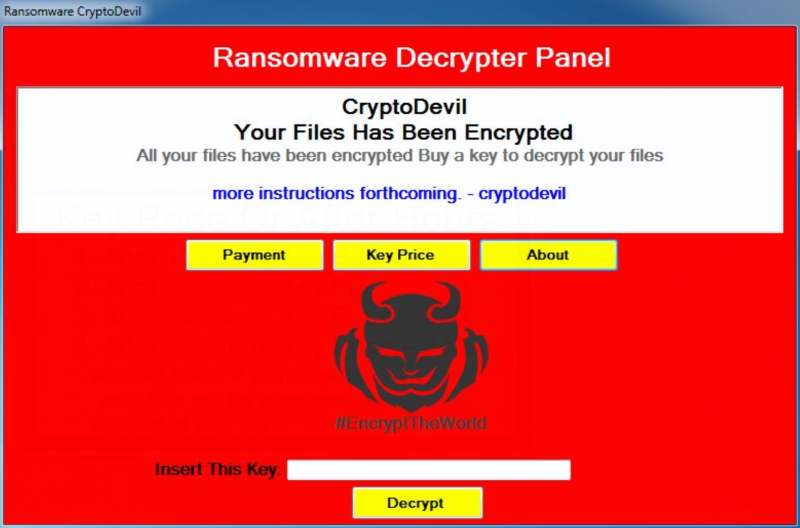
In a real ransomware attack you typically don’t learn about it via a message in your email. You realize something is up when you can’t access anything on your computer and you’re locked out with a ransomware demand screen:
Protecting Yourself from Both Fake and Real Attacks
In the case of the fake email spam bluff, if they show you a password you still use anywhere, obviously, go change it, everywhere.
You should be using password managers or some other system that enables you to use complex, unique passwords across every website.
By using email canaries: the practice of setting up either a dedicated domain name with a unique email address for every vendor (i.e. hairclub4men@markjr.org), or else unix “+” notation (i.e. markjr+hairclub4men@jeftovic.org) – then you can tell which vendor was compromised from the email used to send you the spam, and now you also know that they’ve been storing their customer passwords in cleartext. (The problem with the latter method is not all online forms allow “+” notation in email addresses, and not all mail servers handle it properly. easyDNS mail servers and email forwarders handle them as expected.)
In the case of a real ransomware file-locked situation it all comes down to whether or not you have backups, and have those backups been locked as well?
If you have no viable backups, you’re pretty well stuck paying the ransom. Once you decrypt your files, chalk it up to the cost of learning your lesson and then right away go get some backups happening.
easyBackup specifically screens for all major malware and ransomware variants and syncs with all major malware detection. It’s an incremental backup system so if you get infected you can rewind back to your most recent clean backup, which can itself be encrypted (with your keys, not the attackers), and restore your files.


Hey Mark, Very informative…thx R
I’m a huge fan of the email canaries. Managed to bust Dropbox, VMWare, Steam, and a few other big names.
However, I find that when I notify them, in very clear language, I always get a clueless response of: “no, we are not sending you spam.” I even had VMWare tell me that I had only been a customer as of recently, to which I sent then screenshots from their own website showing licenses dating back more than 10 years. I finally had to go to TrustE to challenge their website’s security certification before I could get a minimally coherent response from them.
Thanks.
The ones I’m getting are definitely coming via LinkedIn – which I know, because I’m fairly obsessive about setting up site-specific forwarding accounts whenever I register an account with a third-party website, and the extortion scam EMails are coming to an address that I setup specifically/only for my LinkedIn account.
Great info, Mark, much appreciated.
I received one of these emails over the weekend. I was a little nervous when I saw the old (ancient, actually) password listed in the email but I became decidedly less nervous when I read on. That bit about taking a snapshot through the camera on my “device” was the tip off: none of the computers I use to access the Internet have a camera. (Other than my phone but I’m not visiting sites that require a login using my phone.) I haven’t stored password in any of my browsers since I began using a password vault—several years ago. I used the arrival of the email as a reminder to change all my online account passwords. And made a note to do it whenever I’m changing my smoke detector batteries.
“In the case of a real ransomware file-locked situation it all comes down to whether or not you have backups, and have those backups been locked as well?”
The question is, how do you know if your backups have been locked as well? Is there a way to tell, so you can figure out just how far back you have to go to find a good backup?
I suspect the ones I’ve been getting (to 2 of my E-mail forwarders) were sourced from the Payless Shoes website. I seem to recall setting up 2 accounts there at different times and one of them might have used the less commonly used forwarder. (These were both from before I set up a special E-mail address for every web site so I can’t be 100% sure if that’s it.) When I went to log in at the Payless site I found neither E-mail address had an account associated with it so maybe they purged them from inactivity. (Though Payless was sending E-mail to one of them until about a year back.) So I suspect somebody physically got their hands on one of the old Payless Shoes servers that had been de-commissioned and found a bunch of E-mail/Password sets on it including E-mail/Password pairs no longer in use on the active site and those got circulated. (The password they had associated with the less used E-mail had not been used anywhere since 2006 so was most likely from a forgotten duplicate account.)
I can rule out Linked In as I’ve never had an account on there.
I’ve been busy changing passwords on a lot of old sites I haven’t used in a while or simply had so long I had from before I started generating a special password for every site. So if anything this was a good reminder to do so but also a near miss on the E-mail/Pasword pair falling into the hands of someone more thorough and them hijacking accounts before I changed the password.
So far I’ve had so many people claim to be watching my web cam that I should sell advertising space on a sign posted in front of it, my ratings might be higher than some Main Stream Media outlets so I might as well cash in… ^_- If only I could find where this mythical web cam is… 😀 Also not sure how this many people are watching through the 0.5Mbps upstream bandwidth I have…it must be magic… ^_-
Anyways, thanks for giving everyone the heads up on this.
This is the first time I heard of email “canaries”, but I realise I have been using them for 15 or 20 years now. They allowed me to sort incoming email by “To:”, identify which email address were on spam lists, put the compromised addresses in my filters, and create replacement ones as needed. If a sender makes an error in the first part of the address I still get it. My only observation is that fewer email addresses are compromised than was the case ten years ago, and that some of the compromised email addresses continue to get spam after a decade has passed.