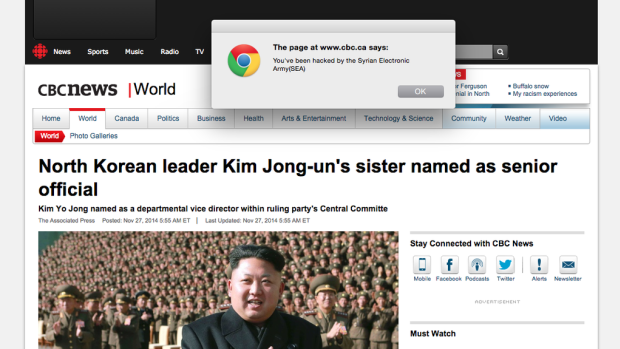
Second time in a week a high profile domain name has been hijacked at it’s domain registrar and used to redirect it’s DNS. First it was craigslist.org, which was hijacked at Network Solutions a few days ago, now the Syrian Electronic Army hijacked gigya.com – a user tracking platform, which they parlayed into the ability to hack 700+ media sites, including the CBC.
We’ve said it before folks, you can have all the intrusion detection, firewalls and DDoS mitigation in the world sitting in front of your infrastructure, you can even be using the most advanced nameserver platform in the world for your DNS 🙂 But that’s all useless if somebody can just bluff (social engineer) or hack their way into your domain registrar and simply pull the rug out from underneath everything by hijacking your domain name.
And to put it, diplomatically, some registrars are easier to do this with than others. If you follow these stories, certain Registrars’ names come up frequently. [ Edit: We’d be hypocritical if we didn’t acknowledge this one: The Government of Ontario domain hijackings ]
For your important domains you need to use account ACLs, you need 2-factor authentication and most of all you need account event notifications, so when somebody makes a move against your domains, you want to be hearing about it from your Registrar, not seeing it on Reddit.
All of these tools are available under your Security settings in your easyDNS account, and while our password and account access recovery process annoys a lot of people for being excessively anal and cumbersome, we’ve never had a domain hijacking occur in the history of the company. Just sayin’.


Leave a Reply