We are happy to unveil a beta feature for email forwarding:
You can now optionally add GPG keys to individual mailmaps so that your forwarded email arrives at its next hop encrypted.
This means that if you are forwarding your email to your ISP, office, or third party email provider (including easyMail by easyDNS), the email will arrive on those servers encrypted and can only be decrypted by entering the passphrase to the corresponding private key.
The email address on the GPG key used does not need to match the address in your mailmap, you can use any public key you want and you could even generate a specific key for each mailmap you want to do this with.
Why Would You Want To Do This?
There is a school of thought that says if you’re not doing anything wrong then you should have no problem accepting that your communications are wiretapped by government intelligence agencies and stored in large databases where they will ostensibly never be used to your disadvantage in any way.
That school is plainly and simply wrong and that’s not an opinion, it’s an historical fact that when the government begins wholesale spying on its own subjects, the road to tyranny has been embarked upon.
The way we see it, if the NSA can do it now with zero due process and total impunity, it just green lights every other law enforcement agency, intelligence organization or even private interests to do the same. In other words, all bets are now off in terms of expectation of privacy in your personal and business communications, so everybody who is concerned about it needs to start taking action on their own to reclaim that expectation.
Our job now is to provide you with tools to help with that.
How to enable easyCrypto™ Mail Forwarding
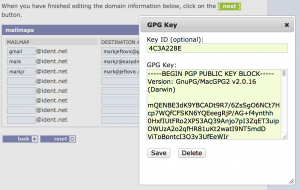
In this initial beta stage we are going to assume that you have a basic knowledge of PGP/GPG, that you know how to generate new key pairs, and that you already have a method for reading your encrypted email, such as a GPG enabled mail client or webmail system.
For those totally new to this, hang in there. We cannot provide support on things like generating keypairs or adding GPG plug-ins to your mail client. If there is a enough demand we will be developing tools to make those steps accessible to the non-technical user as well.
To start using encrypted forwarding, do the following:
- The feature is currently designated beta, so make sure you have beta features enabled in your personal info section
- Your domain needs to be at DNS Hosting level or higher. They breakdown as follows:
- DNS Hosting: 1 crypto address
- DNS Pro: 5 addresses
- Enterprise DNS: 10 addresses
- In the Email Preferences section of your account preferences you enable Encrypted Forwarding
- Edit your mailmaps, enter the public GPG key in the maps you want to encrypt
- Set your primary MX handler to mx-crypt.easydns.com
That’s it. Give about 5 to 10 minutes for the remote mx-crypts to rehash their local keychains and then you should see messages to those mailmaps start arriving encrypted.
How It Works
We’ve modified our MTA (postfix) to lookup a corresponding key entry for inbound email’s envelope-to, if it finds one, it passes the email through a process to use the designated GPG key to encrypt it; then it hands it off to our normal mail-mapping interpolation where the mail is sent to the next hop for a given mailmap’s destination.
Next: Given that the bulk of the widespread systemic NSA surveillance is happening in the USA, and that the NSA and that our own Communications Security Establishment Canada (CSEC) are such cosy pals, we’re just going to assume that the same thing is happening here (and it’s just a matter of time before somebody blows the lid off of it).
We then assume that major Canadian network exchanges, like 151 Front are being vacuumed so we’re deploying mx-crypt.easydns.com forwarders outside the US, outside Canada into datacenters where our comfort level is higher than it is here. Right now we have one POP in (ironically) Eastern Europe and we are working on another one in Switzerland. There will be more to follow.
We round-robin the host records for mx-crypt, so the ingress of cleartext mail into the system is pseudo-random. Maybe a given piece of email comes in via Switzerland, maybe Singapore. The mx-crypt units encrypt those emails (passing through anything with no corresponding keys) and it all gets shunted to the next hop after processing.
Important: This is not an end-to-end encryption solution.
Email sent in the clear can be vacuumed and copied at any step of the way until it hits our mx-crypt message handlers. It’s impossible to know for sure if your cleartext got scooped along the way, the scope of the NSA programs are truly mind-boggling. But they can’t suck up everything (can they?) and also there is the matter of some other agency coming along later and snooping around your ISP or your mail host’s systems.
Once the messages hit those instances they are encrypted using the public keys you attach to your email forwarders before they are shunted onto the destination of your mailmaps. It could be easyMail here on easyDNS or else back to your ISP, Gmail, wherever. But they arrive already encrypted and will remain so while they sit on your mail host’s system.
Then you use your normal GPG client when you read your messages. (For example I use Postbox with the Enigmail plugin and it works totally seamlessly)
This is just the first step.
At the moment this is only available on email forwarding, we’ll be adding it to easyMail and easyMail forwarding soon. Then we’ll be working on more easyCrypto features for your privacy and peace of mind.



Update:
http://www.foxnews.com/politics/2014/01/23/independent-federal-review-board-says-nsa-phone-data-collection-program-should/?cmpid=NL_morninghl
Hooray for liberty and democracy! It is a start, at least. Of course this could just mean the NSA will get the opportunity to do the same thing, just in total secrecy again. But the simple fact that more in DC are recognizing that it is illegal, is a good thing. Yet it could be an attempt to manage the legality in the executive branch, specifically to avoid some more binding Supreme Court case. With spy stuff, of course, things are often not what they seem. But the Supreme Court really shouldn’t be needed for this. The 4th Amendment makes it pretty damn obvious that this is unconstitutional, without 9 learned justices having to comment. (But that had been said of the 2nd Amendment, too.)
It is mainly some people in the legislative and executive branches that need the 4th Amendment reminder, and perhaps this board’s opinion will be enough to bring some of them back from ‘the dark side’. (I really wonder if some of them are just plain cowards – not a political or constituent thing, but a desperation that their own offices will be impacted by a terrorist attack, and so they subjugate the Constitution to save their own skins….this is one more good reason to let legislators telecommute from their home districts, which would reduce MANY conflicts of interest…we have the technology, and maybe that’s what they should do with all the servers they won’t need any more.)
I was particularly happy to see this in the report, about 9/11: “The failure…stemmed primarily from a lack of information sharing among federal agencies, not of a lack of surveillance capabilities,” the report said. “This was a failure to connect the dots, not a failure to connect enough dots.” Amen!
– JH